ABB announced today that Wibu CodeMetter has vulnerable parts.
On the 8thof Sep2020, a series of vulnerabilities affecting CodeMeter Runtime from WIBU SYSTEMS,were made publicthrough WIBU security advisories web site.Products using this servicemight beaf-fected by one or more of the Common Vulnerabilities and Exposures (CVEs)listedbelow.ABB isevaluating the potential impacts on a number of products and has initiated our vulnerability han-dling process to ensure any product related issues are properlyaddressed. With this announcement from WIBU SYSTEMSit is understoodthat ABB will need to integratepatches or fixes to address these vulnerabilities in the CodeMeter Runtimefor products which are affected, according to the ABB Vulnera-bility Handling policy. We are currently analyzing our product portfolio for exposure.Potentially affected customersshould expect additional communication or advisories as more details become available.
The vulnerability CVE numbers and CVSS scoresare listed in the table below:
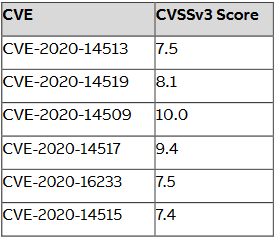
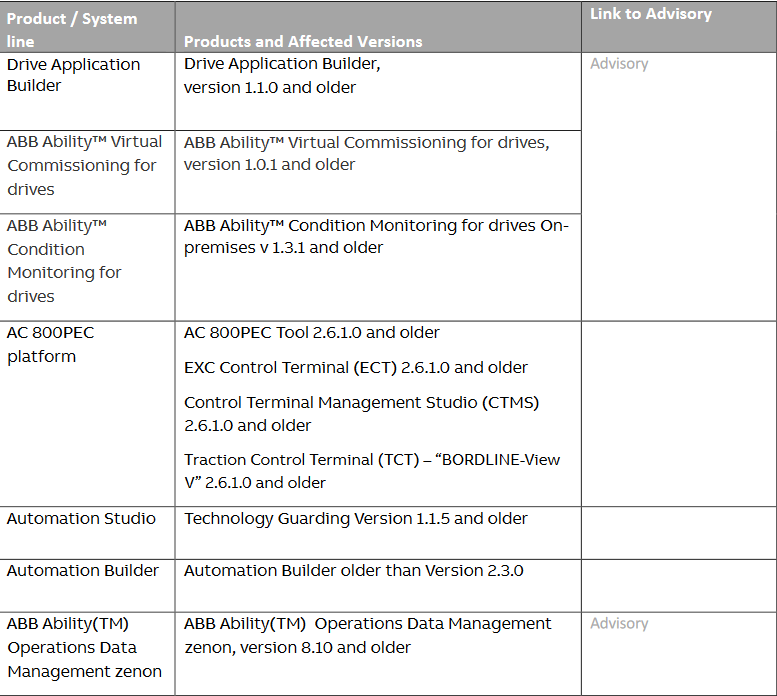
The products listed in the table are affected by the vulnerabilities listed. ABB continues to evaluate the vulnerabilities and will update the notification when additional information becomes available
Recommended security practices and firewall configurations can help protect an industrial control net-work from attacks that originate from outside the network. Such practices include ensuring that protec-tion, control & automation systems are physically protected from direct access by unauthorized person-nel, have no direct connections to the Internet, and are separated from other networks by means of a firewall system that has a minimal number of ports exposed, and others that have to be evaluated case by case.
In general protection, control & automation systems should not be used for general business functions which are not critical industrial processes. Portable computers and removable storage media should be carefully scanned for viruses before they are connected to a control system. Block all non-trusted IP communications.To minimize the risk of exploitation of the CodeMeter vulnerabilities users should take these defensive measures:
- Locate the control system network behind a firewall and separate them from other networks.
- In environments where CodeMeter network license server is not in use, configure firewall to block access to portTCP 22350
- Block anomalous IP traffic by utilizing a combination of firewalls and intrusion prevention sys-tems.
- Disable or block IP tunneling, both IPv6-in-IPv4 or IP-in-IP tunneling.
- Avoid exposure of the devices to the Internet and use secure methods like VPN when accessing them remotely.
