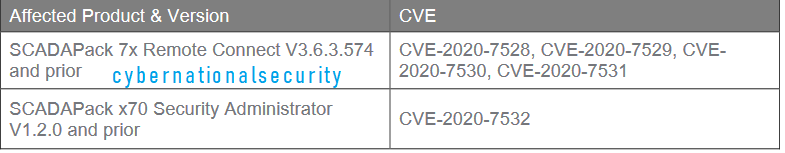
Schneider Electric is aware of multiple vulnerabilities in SCADAPack 7x Remote connects and SCADAPack x70 Security Administrator applications.
CVE ID: CVE-2020-7528CVSS v3.0 Base Score 6.1 | Medium | CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:L
A CWE-502 Deserialization of Entrusted Data vulnerability exists which could allow arbitrary code execution when an attacker builds a custom .PRJ file containing a malicious serialized buffer.
CVE ID: CVE-2020-7529
CVSS v3.0 Base Score 5.5 | Medium | CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N
A CWE-22 Improper Limitation of a Pathname to a Restricted Directory (‘Path Transversal’) vulnerability exists which allows an attacker to place content in any unprotected folder on the target system using a crafted .RCZ file.
For SCADAPack 7x Remote Connect and SCADAPack x70 Security Administrator these vulnerabilities are fixed in SCADAPack 7x RemoteConnect V3.7.3.904 and SCADAPack x70 Security Administrator V1.6.2 respectively and are available for download in the link below, as part of the RemoteConnect V2.3.2 package:
There is no need to reboot. The following workarounds and mitigations can be applied by customers to reduce the risk:•Educate users to screen files from external sources and avoid files from untrusted sources before opening them in RemoteConnect or Security Administrator.
SCADAPack 7x RemoteConnect is a single software tool for users to monitor, configure, program, and commission SCADAPack 470, 474, 570, 574, and 575 Smart RTUs (Remote Terminal Units).
General Security Recommendations
We strongly recommend the following industry cybersecurity best practices.
- Locate control and safety system networks and remote devices behind firewalls and isolate them from the business network.
- Install physical controls so no unauthorized personnel can access your industrial control and safety systems, components, peripheral equipment, and networks.
- Place all controllers in locked cabinets and never leave them in the “Program” mode.
- Never connect programming software to any network other than the network for the devices that it is intended for.
- Scan all methods of mobile data exchange with the isolated network such as CDs, USB drives, etc. before use in the terminals or any node connected to these networks.
- Never allow laptops that have connected to any other network besides the intended network to connect to the safety or control networks without proper sanitation.
- Minimize network exposure for all control system devices and systems, and ensure that they are not accessible from the Internet.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs). Recognize that VPNs may have vulnerabilities and should be updated to the most current version available. Also, understand that VPNs are only as secure as the connected devices.
